Detect emulators, spoofed fingerprints, and automation bots so large-scale fraud never mimics real user behavior.
Detect emulators, spoofed fingerprints, and automation bots so large-scale fraud never mimics real user behavior.
FOCAL Enterprise Fraud Management combines device and behavior intelligence to expose virtual rigs and spoofed fingerprints that try to masquerade as real users.
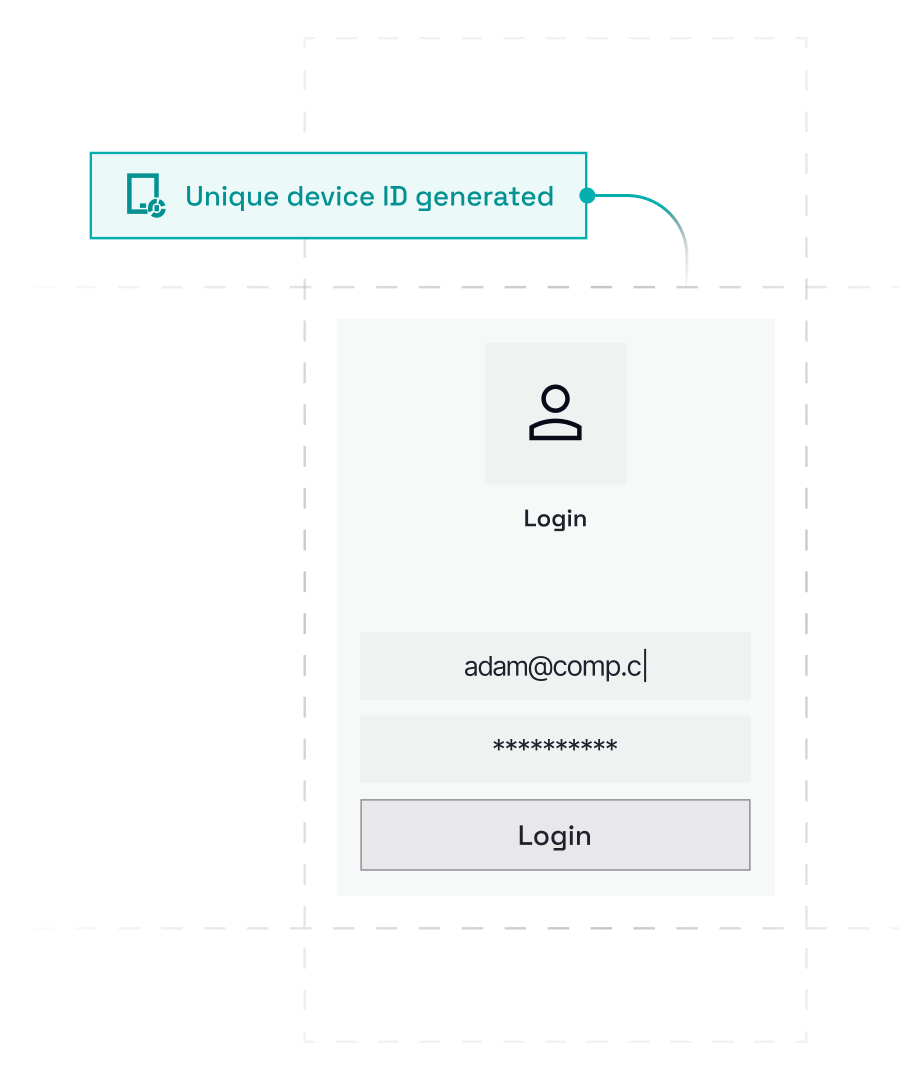







FOCAL is built to protect digital platforms from modern fraud across onboarding, in‑app journeys, and payments.
FOCAL is built to protect digital platforms from modern fraud across onboarding, in‑app journeys, and payments.
Hear how FOCAL is helping compliance teams work faster and reduce risk.
Secure logins, in‑app sessions, and payments in real time with FOCAL Enterprise Fraud Management.