With a persistent Universal ID, it proactively identifies frauds such as account takeover attempts, mule activity, and jailbreaking cutting false positives while keeping genuine customers’ access seamless.
With a persistent Universal ID, it proactively identifies frauds such as account takeover attempts, mule activity, and jailbreaking cutting false positives while keeping genuine customers’ access seamless.
Identify a device’s identity, configuration, and network context the moment it turns suspicious, so high‑risk activity can be stopped before it turns into fraud losses.
Generates a persistent fingerprint for every device from 30+ hardware, software, network, and behavioral signals. It stays stable even after app reinstalls, OS updates, IP changes, or basic factory resets, and resists common spoofing attempts.
Maps connections between devices, accounts, and IPs to uncover coordinated rings and mule networks using shared attributes, outlier scores, and network clustering.
Combines device attributes with IP reputation and geo‑intelligence to distinguish trusted environments from risky ones.
Scores every login and registration in milliseconds by combining device signals, behavioral biometrics, and threat intelligence for decisioning.
Triggers instant Approve/Review/Reject actions blocking high-risk devices and flagging accounts based on 100+ pre-built rules.
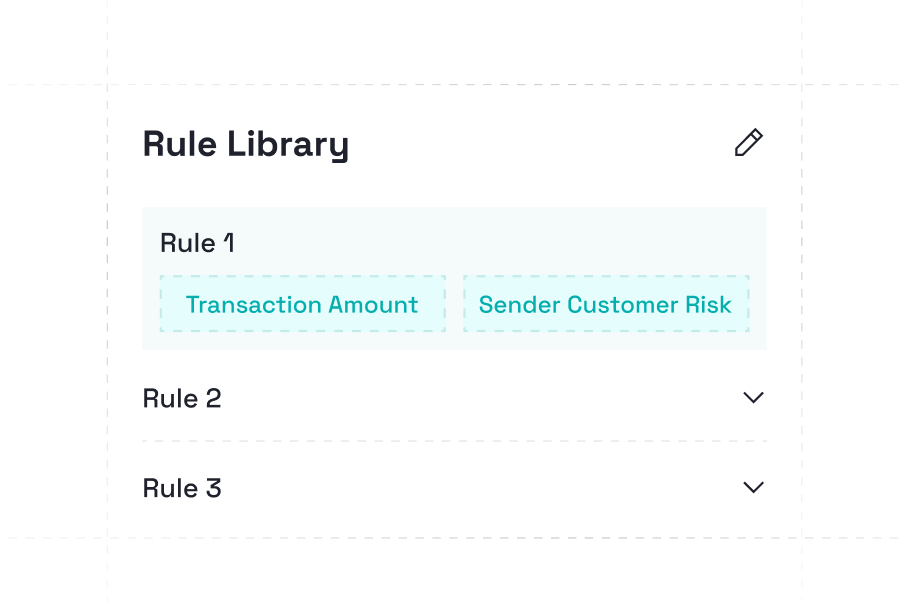
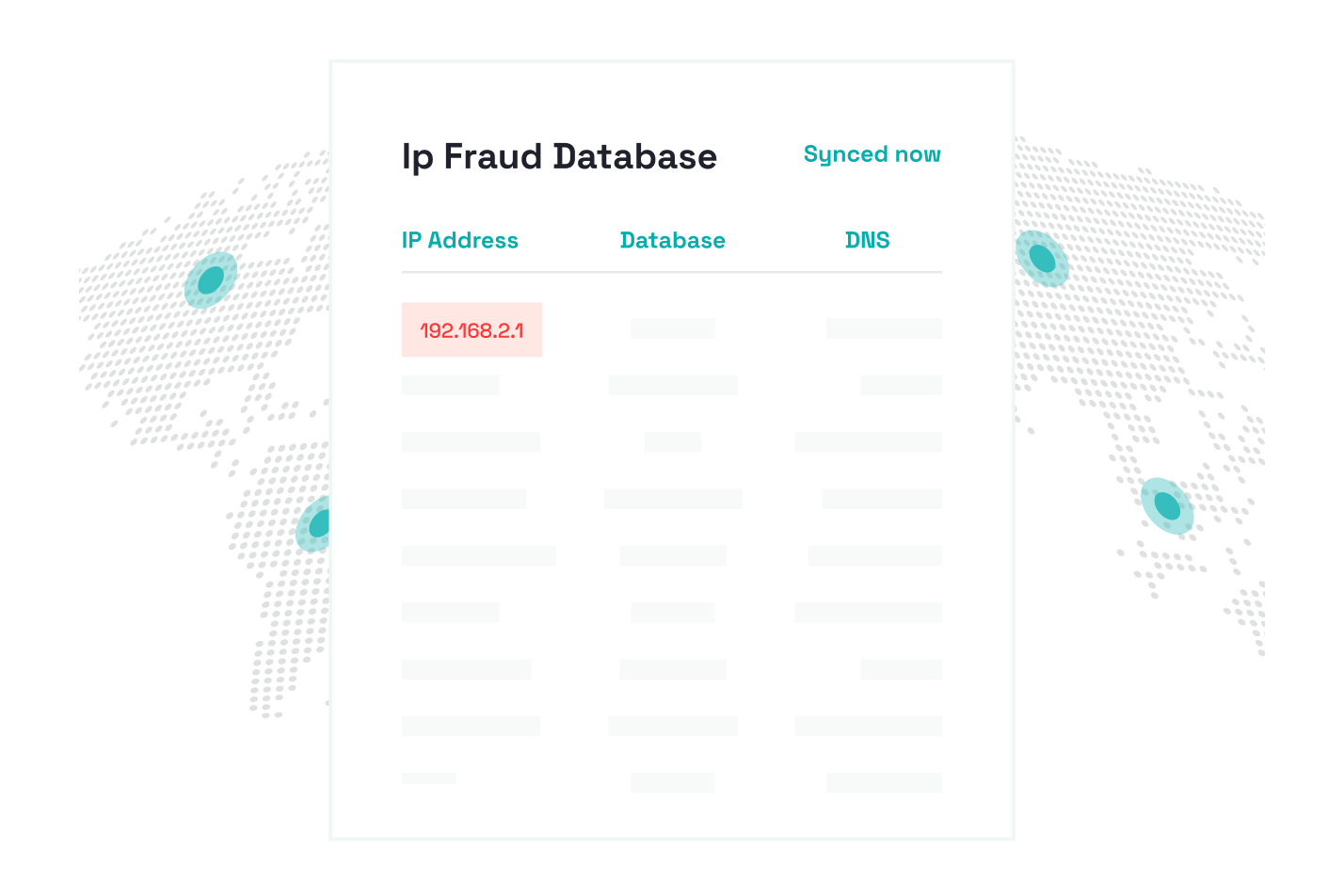
Applies granular blacklists/whitelists so known bad devices and IPs are stopped at the source while trusted entities bypass unnecessary checks.
Provides a centralized dashboard with automated prioritization, 360° customer views, and compliance-ready reporting for streamlined investigations.
FOCAL Device Intelligence continuously fingerprints every device into a persistent Universal ID and scores its network context, exposing hidden device‑based fraud while keeping trusted users access fast and low‑friction.
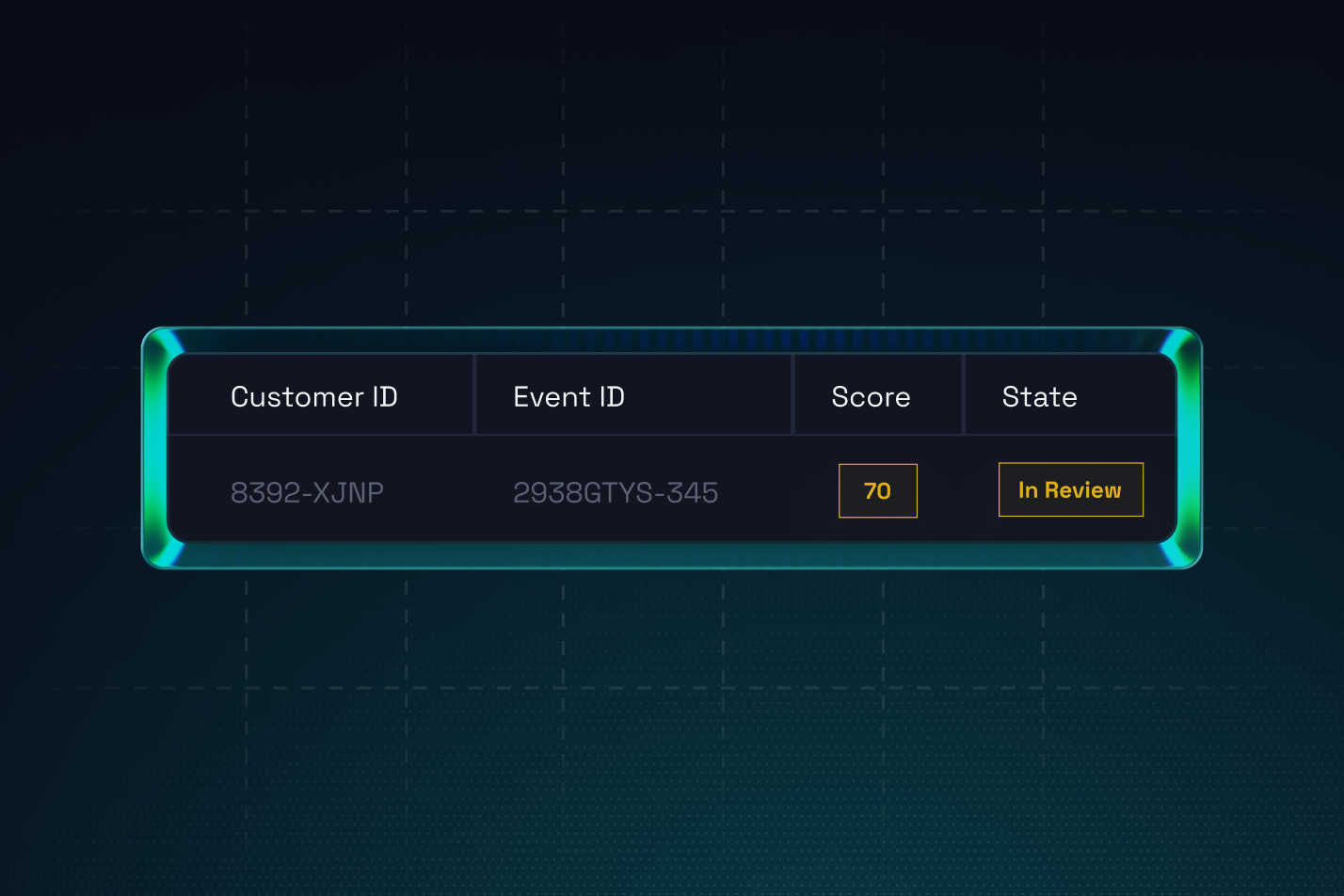
Explore how FOCAL Device Intelligence fingerprints every device, uncovers emulators and hidden connections, and gives fraud teams real‑time risk scores so they can stop high‑risk sessions without slowing trusted customers.
